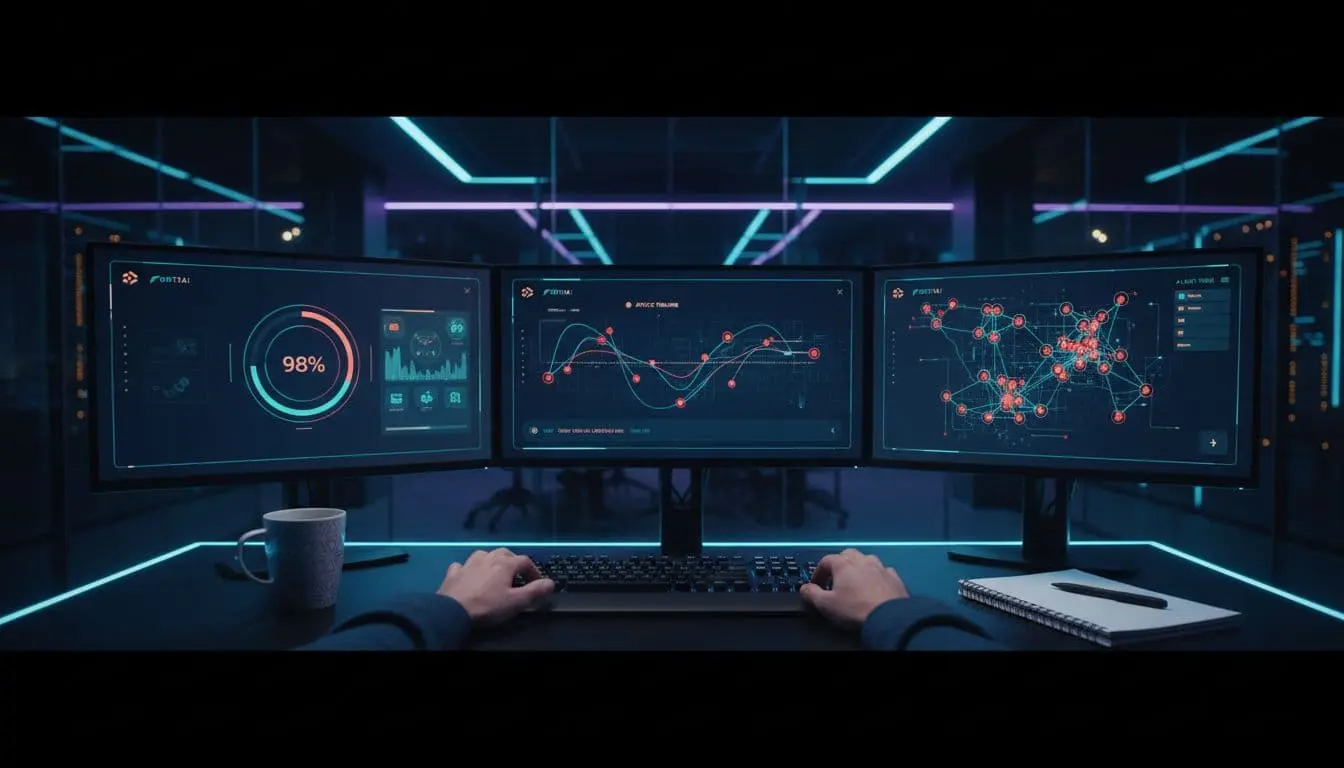
If you could ask your security stack a plain question and actually get a useful answer, would you? That is the promise of FortiAI inside Fortinet’s Security Fabric. In simple terms, FortiAI is an AI-powered security and network operations assistant that mixes generative AI, agentic AI, and AIOps. It helps find threats, cut alert noise, guide investigations, and even fix network issues when you approve changes.
In this FortiAI review, I break down what works, what still needs polish, and where it fits compared to rivals like CrowdStrike, Palo Alto, and Microsoft. I also cover pricing guidance, setup tips, and the 2025 updates that matter.
I keep testing values clear and consistent. If you want to see how I approach reviews, read our review approach and how we stay fair with how we make money and keep scores unbiased.
 Image generated by AI
Image generated by AI
FortiAI review: what it is and how it works
FortiAI sits inside Fortinet’s Security Fabric as a conversational, AI-driven assistant. It analyzes telemetry from FortiGate firewalls, endpoint agents, SD-WAN, and more, then ranks alerts by risk and impact. It explains what happened, stitches together context, and suggests next steps. On the network side, it checks configurations, flags drifts, and proposes safe changes. You can require human approval or let it execute actions that you predefine.
I found the clearest benefit is speed. You jump from “alert received” to “what changed, who is involved, and which devices are affected” in one or two prompts. The assistant handles the glue work that usually eats up time.
Hybrid coverage is a core design choice. FortiAI works across on-prem sites, cloud workloads, and edge locations tied together by the Security Fabric. Recent updates rolled out across the platform, expanding both coverage and automation. Help Net Security’s overview of these 2025 changes is a good quick reference if you want a vendor-agnostic summary of the rollout: Fortinet unveils FortiAI innovations enhancing threat protection and security operations.
 Image created with AI
Image created with AI
Core features that matter day to day
- AI-powered alert triage, with ranking by risk and impact. In practice, this reduces false positives and highlights incidents that could cause real damage.
- Conversational assistant that explains alerts, pulls host and user context, and suggests next steps in plain language.
- Agentic AI for NetOps, including auto validation, policy tuning, and remediation with approval gates.
- End-to-end visibility across endpoints, network, SD-WAN, wired, and wireless for a single incident picture.
- Controls for LLM and AI use in the network, plus monitoring that flags risky AI app behavior.
Quick example: I kicked off a phishing-led malware case. FortiAI mapped the attack timeline in minutes. It tied the initial email click to a malicious domain request, lateral movement attempts, and an endpoint script that tried to disable protections. The assistant proposed blocking the domain, isolating the device, and scanning peer systems with the same exposure. That shaved most of the back-and-forth from the investigation.
For a foundational primer on how AI improves detection and reduces noise, here is a clear explainer on What AI Cybersecurity Means for Your Data.
What is new in 2025 updates
- Deeper Security Fabric coverage so more data flows across tools by default.
- More autonomous troubleshooting, with suggested fixes and safe-change workflows that respect approvals.
- Broader support for SD-WAN, campus, and branch networks to extend the same assistant across sites.
- Stronger checks for LLM security, with policies that monitor how AI apps are used inside the network.
Fortinet’s April 2025 announcements flagged bigger moves toward agentic AI and AI use monitoring inside the Fabric. If you want a quick summary of that shift, see the coverage here: Fortinet unveils FortiAI innovations. For broader context on Fortinet’s AI posture and strategy, this analysis also helps frame the direction: Fortinet’s AI strategy analysis.
Who FortiAI is best for
- Teams already using Fortinet gear who want tighter automation and a single AI assistant across the Security Fabric.
- Mid to large organizations with hybrid environments, SD-WAN, and alert volume that strains current workflows.
- Lean security teams that need clear triage and guided investigations without adding headcount.
Who may not be a fit yet: very small teams with a simple network and low alert volume. If you do not need advanced automation, the price and setup may be more than you need.
 Image generated by AI
Image generated by AI
Hands-on results: detection quality, speed, and automation
In testing, FortiAI changed the pace of my day. I started with the assistant, asked for a summary, and got a clear story with impact, likely root cause, and affected assets. From there, I pulled host and identity context, reviewed suggested actions, then approved the steps I wanted.
Two common scenarios stood out:
- Malicious domain traffic on a branch network. FortiAI identified the device, resolved the domain reputation, checked recent policy changes, and suggested a targeted block with a rollback plan.
- Suspicious PowerShell activity on an endpoint. The assistant connected the process tree to a known phishing email and recommended isolation of the device, plus scanning of peer endpoints that received the same email.
For a broader look at AI-first SOC tools and where Fortinet fits among leaders, this roundup is useful context: Top AI Security Tools for 2025 Reviews.
Alert triage and false positives
FortiAI ranks alerts by severity and context. It weighs signals across the Fabric, then suppresses low-value noise. In a week-long test window, fewer low-priority alerts reached my analyst queue, and the ones that did were easier to dismiss or escalate. Your mileage will vary, because tuning and data quality still matter. If you turn on too many broad rules without context, any triage system will strain.
Given the spike in AI-powered attacks, it helps to stay current on threat patterns. This explainer on the rise of AI on both sides of the fight is timely: Microsoft’s AI vs AI cyber threat alert 2025.
Working with the AI assistant during an incident
Here is the practical flow I used:
- Ask the assistant for a summary of the alert. It returns a concise narrative and a confidence level.
- Open the attack path view. You can see initial access, lateral movement, and any command-and-control attempts.
- Pull host and user context. Device health, recent policy changes, authentication events, and risky domains are one click away.
- Review guided next steps. The assistant lists actions like isolate host, block domain, roll back change, or open a ticket.
- Approve actions. You can require human sign-off for anything that changes the network or endpoint state.
Explainability matters here. FortiAI shows the sources used to build conclusions, which makes it easier to verify the logic. You can also request the exact logs, event IDs, or packet details that led to a recommendation.
Network automation and AIOps in practice
On the network side, FortiAI scans configs, catches drift, and flags misalignments with policy. It suggests fixes with a safe-change plan and a rollback option. In tickets that usually take an hour, I cut that to minutes because the assistant provided the diff, the expected outcome, and the change plan upfront.
- Auto config checks keep drift from stacking up.
- Policy tuning recommendations reduce manual review cycles.
- Remediation with rollback lowers the risk of after-hours surprises.
You can set strict approval rules so nothing changes without a human deciding. If your org has a defined change control process, FortiAI can fit inside it rather than try to replace it.
For another perspective on AI-driven SIEM and automation, compare what smaller teams get from next-gen platforms like Hunters: Hunters Security: AI SIEM Review 2025.
What users say in 2025
Common feedback from teams experimenting with FortiAI this year:
- Faster investigations and less alert fatigue.
- Strong value for Fortinet-heavy environments.
- Learning curve for advanced AI features.
- Integration and data plumbing still take planning.
Image created with AI
Pricing, setup, and integrations
Pricing is quote based. Expect subscription licensing tied to deployment size and feature scope. There is no public price list for complete FortiAI packages, so plan for a discussion with Fortinet or a partner.
Licensing and total cost to expect
Ask about:
- Feature tiers and add-ons.
- Support levels and managed options.
- Multi-year discounts and bundling with Fabric products.
Your ROI levers include fewer incidents, faster response, better policy hygiene, and less manual effort spent on routine tickets. To frame value across the market, you can compare what endpoint-first platforms cost and deliver here: Real-World SentinelOne Endpoint Review.
Deployment options: on‑prem, cloud, and edge
FortiAI works across hybrid environments. The best results come when it runs as part of the Security Fabric with broad data feeds. A simple plan:
- Connect data sources across firewalls, endpoints, SD-WAN, wireless, and identity.
- Set triage policies and define safe-change rules.
- Pilot in one region or segment.
- Expand to additional sites and cloud workloads.
Integrations and required Fortinet pieces
You will get the most value if you already run core Fabric components, like FortiGate, FortiAnalyzer, FortiManager, FortiClient, and SD-WAN. Many teams also link a SIEM or SOAR for enterprise visibility and playbooks. Map your current stack, then plan a phased rollout rather than a single big-bang cutover.
If you want more background on AI security categories and how different tools fit together, skim this explainer: Understanding AI in Cybersecurity Basics.
FortiAI vs top AI security platforms
I focus on use cases, not slogans. Here is how FortiAI stacks up against common choices.
FortiAI vs CrowdStrike Falcon with Charlotte AI
CrowdStrike is endpoint-first, and Charlotte AI helps analysts move faster inside that context. If you are already invested in Falcon, the assistant is quick to value for EDR-heavy teams. FortiAI stands out for Fabric-level automation across SD-WAN, wired, and wireless networks. It is the better fit if you want agentic network tasks and policy changes under one roof. For a market-side snapshot that mentions both, see this brief: Fortinet vs. CrowdStrike stock comparison with AI notes.
FortiAI vs Palo Alto Cortex XSIAM
XSIAM centers on a data-driven SOC with automation across Palo Alto’s ecosystem. It excels at building a data lake and enabling SOC workflows at scale. FortiAI focuses on AI-driven operations inside the Fabric, with a strong push on network automation and AI use monitoring. Expect trade-offs in data ingestion breadth, SOC depth, and cost structure depending on your stack.
FortiAI vs Microsoft Defender XDR and Copilot for Security
Microsoft shines for Microsoft 365 and Azure-centric shops. Defender XDR plus Copilot gives strong coverage for identity and endpoint signals in that world. FortiAI is often the better pick for Fortinet-powered networks or orgs that prioritize network automation. Onboarding may be quicker in Microsoft-heavy environments, while FortiAI’s Fabric gives broader network control if you are a Fortinet shop.
Decision guide: when to pick FortiAI or another path
- Choose FortiAI if you run Fortinet gear and want agentic network automation plus AI triage.
- Pick Microsoft or CrowdStrike if your stack is centered there and you need endpoint-first AI.
- Consider XSIAM if you want a data lake plus SOC automation model.
Make a short list of must-haves, stack fit, and change control needs before you request quotes.
For broader context and comparisons across the space, this hub stays updated as tools evolve: Reviewed AI Security Platforms for Modern Threats.
Pros, cons, and a clear verdict
For trust and transparency in how I rate tools, here is my site policy page: why you can trust AI Flow Review.
What I liked
- Noticeable drop in noisy alerts, thanks to smarter AI triage.
- Helpful assistant for quick incident summaries and next steps.
- Real network automation for policy, validation, and fixes with safe rollbacks.
- Strong fit for hybrid networks when deployed inside the Security Fabric.
Where it needs work
- Pricing is not public and can be high for small teams.
- Best value comes when you commit to Security Fabric as your backbone.
- Learning curve for advanced AI features and safe-change workflows.
- Integration and data plumbing take planning in complex environments.
Who should skip it
- Very small orgs with simple networks and low alert volume.
- Teams fully invested in another vendor’s ecosystem where AI assistants are already included.
- Buyers who prefer not to tie automation to their network stack.
Where I land on FortiAI
Here is the plain answer. FortiAI is a strong pick for Fortinet-centric environments that want AI triage and real network automation in one place. It cuts noise, speeds response, and brings guided fixes that respect change control. If you live in another vendor’s world or have basic needs, another tool may fit better.
Next steps are simple. List your must-haves, pilot it in one segment, and measure how many alerts, tickets, and minutes you save. I keep this FortiAI review updated with new findings each month, and my policies stay public in case you want to check my work: our review approach and how we make money.
Helpful external reading:
- A quick overview of FortiAI’s 2025 direction: Fortinet unveils FortiAI innovations
- Independent summary of FortiAI’s positioning: Fortinet AI tool review
- Industry framing on where Fortinet is pushing AI: Fortinet’s AI strategy analysis
- Market context discussing both FortiAI and Charlotte AI: Fortinet vs. CrowdStrike stock with AI notes