You can feel it, right? The tempo of cyber threats keeps climbing. In 2025, Microsoft rang the bell: Artificial Intelligence (AI) vs AI is here, with attackers using AI to strike faster while defenders use AI to stop them. Attacks that once took hours now unfold in minutes. Defenses that once crawled now react in seconds.
I answer key questions about what changed, how attackers are using AI, how defenders are adapting, and what I’m doing in the next 90 days to stay ahead. Here is the quick view: Microsoft observes more than 100 trillion security signals daily; phishing and social tricks still drive a large chunk of breaches; and AI boosts both sides of the fight. If you want context and a plan that you can actually follow, you’re in the right place.
Before we dive into tactics, I recommend grounding yourself in the basics of cybersecurity. If you need a primer on modern defenses, my overview of AI cybersecurity fundamentals is a handy refresher.
Microsoft’s 2025 alert: what the AI vs AI surge means right now
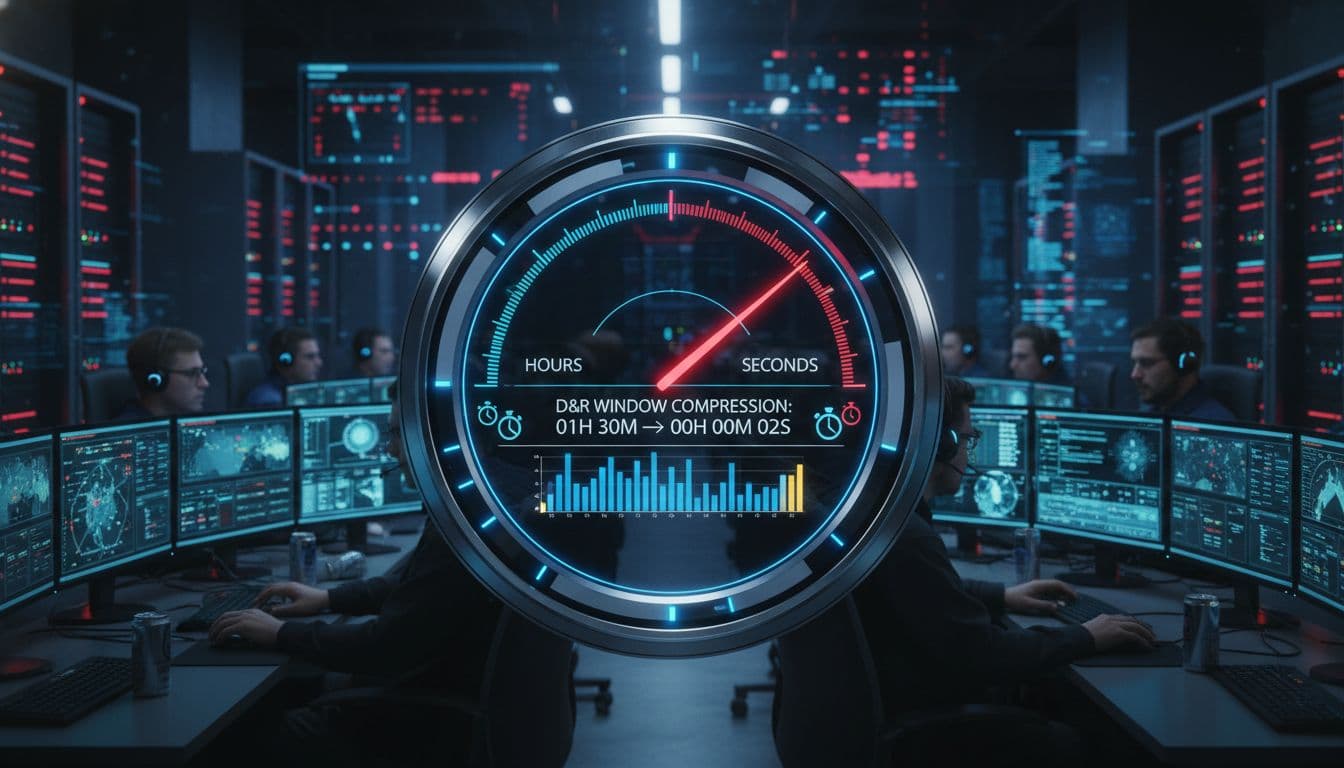 Image generated by AI.
Image generated by AI.
Microsoft’s latest guidance lands hard: AI now powers both attack and defense, which raises speed, scale, and complexity. The last year changed the game. Rapid AI adoption has made generative AI tools easy to access, attacker skill requirements dropped, and cooperation between state actors and cybercriminal groups got tighter. That mix produces rapid campaigns, stealthy operations, and harder investigations.
This matters to anyone who builds or runs systems. There is real economic risk from downtime, data breaches, and data loss, and privacy harm from stolen identity and synthetic media. Safety is at stake when critical systems are targeted. In short, we cannot treat this as a future issue. It is present tense.
If you want Microsoft’s full analysis, read the Microsoft Digital Defense Report 2025 and the companion view in the security insider overview. I found the PDF helpful for deep detail too, especially on attacker playbooks: download the report.
The big picture: AI supercharges both sides
Microsoft processes more than 100 trillion daily security signals using machine learning. That scale makes trends visible early. Deep learning helps defenders correlate patterns, enrich alerts, and flag outliers across endpoints, identities, and cloud workloads.
Yet the same technology helps attackers. AI automates content creation, personalizes lures, and adjusts code on the fly. It also speeds up discovery of weak spots. The result is a race where both sides iterate in near real time. Microsoft reports that response windows have shrunk from hours to seconds with AI-driven containment. Attackers make their moves just as quickly.
For ongoing threat intel beyond the annual report, I also keep an eye on Microsoft’s Security Intelligence hub, including tools like Security Copilot.
What changed in the last 12 months
- Generative AI is easier to use. Attackers spin up scripts, phishing kits, and synthetic media in minutes.
- Tooling got accurate enough to tailor lures at scale, across email, SMS, voice, and video.
- State groups and criminal gangs share tactics and attack infrastructure more often, which blurs attribution and boosts stealth.
One more sobering note from Microsoft’s communications this year: extortion and ransomware remain dominant. See the breakdown on how these tactics drive more than half of incidents in Microsoft’s summary, Extortion and ransomware drive over half of cyberattacks.
Why this matters now
The consequences are not abstract. They show up as faster ransomware, broader data theft, and influence operations powered by synthetic media. They show up as real dollars lost and trust eroded. When criminal and geopolitical motives overlap, every sector becomes a potential pressure point. That includes small organizations that link into supply chains.
If this feels heavy, take heart. There is a path forward, and it is practical. Start by strengthening identity, add smart automation, and build muscle memory for fast incidents.
How attackers weaponize AI vs AI to beat defenses
 Photo by cottonbro studio
Photo by cottonbro studio
Here is how the bad side uses AI today. These patterns are common across sectors and sizes.
- Faster phishing and social tricks
- Smarter malware and rapid exploit discovery
- Attacks against the AI pipeline itself
- Ransomware that moves in minutes
If you are considering defense tools that can see these moves as they happen, my roundup of top AI security tools for 2025 covers strong picks for detection, investigation, and containment.
Faster phishing and social tricks
Phishing and social engineering still drive a large portion of breaches, roughly a quarter to a third by many public estimates. AI makes them sharper. It crafts emails in a target’s tone, polishes grammar, and mimics voice or video. The result is higher click rates, more credential theft, and more initial footholds.
A quick example: a fake invoice email references a real project, uses the right signature, and appears at the right time. The attachment could be a seemingly innocent SVG file, and the link leads to a login page that looks perfect. Without phishing-resistant MFA in place, one click can hand over the keys.
Smarter malware and quick exploit discovery
Malware now adapts mid-run. With AI guidance, it can change behavior to avoid the model that just flagged it. It employs obfuscation by shifting process names, sleep times, or network beacons to slip past rules. Pair that with AI that scans code for weakness, and attackers can spin up scripts and kits quickly using AI-generated code, chaining bugs faster than many teams can patch.
Speed is the theme. When weaknesses are found quickly, time to exploitation drops. That is why early detection and automated containment matter so much.
Attacking the AI itself: prompts, data, and models
This is the new front line. Three simple ideas help explain it:
- Prompt injection: an attacker feeds instructions that override your app’s intent, so the model leaks data or performs a risky action.
- Data poisoning: bad data is mixed into training or retrieval sources, so the model learns the wrong patterns.
- Model manipulation: direct tampering with model weights or guardrails, often through exposed endpoints or stolen keys.
The risks include data theft, unsafe outputs, and models that take actions they should not. If you run APIs and LLM apps, an API security layer helps map data flows and detect odd behavior. I reviewed one such platform here: Salt Security API discovery review.
Ransomware at AI speed: minutes matter
Here is a snapshot that stuck with me. A global shipping company faced a ransomware push that unfolded in minutes, not hours. Lateral movement was scripted and fast. AI-assisted defense isolated endpoints and segmented network paths in under two minutes, which disrupted the encryption stage and limited the blast radius.
The takeaway is simple. Both sides move at near real time. Preparation and automation decide who wins the minute.
How defenders win: an AI vs AI security stack that scales
Defense is not a single product. It is an AI-powered protection stack in cybersecurity that turns signals into action while keeping people in control. This is the layout I use when I assess programs and select tools.
If you need a sense of how autonomous defense performs in practice, I share test notes in my AI cybersecurity platform Darktrace review, which covers real-time detection and response.
Signals at scale: telemetry and intelligence
Start with visibility. You want broad, high-quality telemetry from endpoints, identities, cloud workloads, SaaS, and network controls. The goal is to correlate events and enrich them with threat intel so you can spot anomalies early for effective threat detection.
Key moves:
- Centralize logs and endpoint telemetry.
- Ingest identity events and sign-in risk.
- Enrich alerts with known actor tactics and infrastructure.
- Flag unusual behavioral patterns, privilege spikes, or data exfiltration.
Autonomous detection and response
Artificial Intelligence (AI) can cut mean time to respond from hours to seconds. It triages alerts, groups related events, and auto-isolates likely compromised assets. Safer Intelligent Automation (IA) keeps human oversight in the loop for high-impact steps, like disabling a global admin account or blocking a core service.
- Autonomous AI auto-quarantines suspicious endpoints.
- Kill malicious processes based on behavior.
- Contain accounts when session risk spikes.
- Require approvals for changes that could disrupt production.
Identity-first defense
Identity is often the front door. Lock it.
- Use phishing-resistant MFA or passkeys for admins and staff.
- Apply least privilege and just-in-time access.
- Rotate and vault service credentials.
- Revoke tokens fast when risk rises.
- Audit dormant accounts and stale app registrations.
These steps reduce the success rate of social attacks and limit lateral movement if someone slips through.
Secure LLM apps: guardrails and red teams
LLM applications need product-grade controls, not just best effort settings.
- Input filtering to catch harmful prompts and prompt injection.
- Output filtering to block sensitive data and risky actions.
- Policy grounding, so answers map to allowed sources.
- Rate limits and abuse throttles.
- Content provenance checks when generating media or data.
- Routine model evaluations against known attack techniques.
Add internal red teams that specialize in prompt injection paths and data leakage routes. Validate not only the model, but also the chain of tools and APIs it can call.
Resilience playbook
Assume something will break. A fast recovery turns an incident into a story, not a disaster.
- Keep backups, including offline copies.
- Segment networks by business impact.
- Test restore time and data integrity.
- Run tabletop drills that simulate fast-moving ransomware and model abuse.
- Pre-stage communication templates for staff, customers, and partners.
Action plan: what I can do in the next 90 days
You can build momentum in three months without boiling the ocean. Here is the plan I am following, which you can adapt to your size and sector.

Quick wins in 30, 60, and 90 days
- 30 days: turn on phishing-resistant MFA for admins and high-risk users, run a phishing drill, inventory LLM apps and exposed APIs, and establish basic risk governance through guardrails like input filtering and rate limits.
- 60 days: enable automated containment for common threats, segment critical systems, and start regular model evaluations for injection and data leakage.
- 90 days: complete a ransomware tabletop with leadership, test restores from clean backups, and close the gaps you found in drills.
For tool selection during this sprint, my guide to reviews of leading AI cybersecurity software shows options that balance visibility and safe automation.
Metrics that matter
Track what proves progress. I use a short list and trend it monthly.
- Mean time to detect (MTTD)
- Mean time to respond (MTTR) and contain
- Phishing failure rate from drills and real phishing campaigns
- Blocked model abuse attempts and prompt injection detections
- Patch or mitigation time for high-severity weaknesses
If numbers improve over a quarter, keep going. If they stall, tune the playbooks and automate another step.
Smart budget choices: buy, build, or blend
I prioritize tools that increase visibility and automate safe response as part of effective AI risk management. For most teams, a blend works best.
- Buy: platforms that unify telemetry and provide trustworthy automation.
- Build: playbooks, policies, and model guardrails that reflect your environment.
- Blend: vendor AI for speed, your rules and approvals for control.
One note from Microsoft’s 2025 report that stuck with me: small teams can match attacker speed by leaning on AI-driven response, but they need strong identity control and clear approval paths. That balance is key.
People power: training for AI-age attacks
Technology does a lot. People close the gap.
- Run frequent simulations that include AI-shaped lures and realistic deepfakes.
- Teach rapid reporting and clear escalation steps.
- Share short, friendly guidance on what to do when a prompt or link feels off.
- Recognize good catches publicly. That nudge improves participation.
A forward path, starting today
Here is the core idea, brought back to the start: AI vs AI speeds up both attackers and defenders. The side that learns and adapts faster wins, and successful adaptation requires people to harness human intelligence to outpace the automated attacks. The stakes are high with cyber threats, from economic stability to privacy and safety, but we have tools and patterns that work.
If you are ready to move, start the 90-day plan today. Harden identity. Add safe automation to detection and response. Secure your LLM apps with real guardrails and red-team practice. And do not do this alone. Partner across teams, lean on trusted vendors, and support responsible AI development, AI accountability, and global cooperation.
For deeper context as things evolve, I keep this page bookmarked for updates: Microsoft Digital Defense Report and Security Intelligence. If you want a simple overview you can share with non-technical peers, my guide to the basics of AI in cybersecurity is a good starting point.
Thanks for reading, and stay sharp. The clock is ticking, but with the right stack and habits, we can match the speed of modern threats and keep our systems safe.